Agility CMS: A Foundation for Better Online Security+

Download the 'Foundation for Better Online Security' Guide
From a corporate point of view, security is the number one consideration regarding the procurement of software and services. We share that point of view when it comes to the security and stability of Agility CMS.
Gone are the days when software could be expected to exist solely behind firewalls or locked inside a limited intranet. The world has become powered by systems that interoperate with each other using strict and secure protocols. Agility CMS lives in that world.
Security Concerns with WordPress
40% of the internet runs on WordPress, a system with many known (and emerging) vulnerabilities and attack vectors. The central problem with WordPress, and other systems like it, isn't just its popularity but with how it interoperates with user systems. Namely, using plugins.
These plugins add to the monolithic codebase that powers a traditional website, making it much more vulnerable.
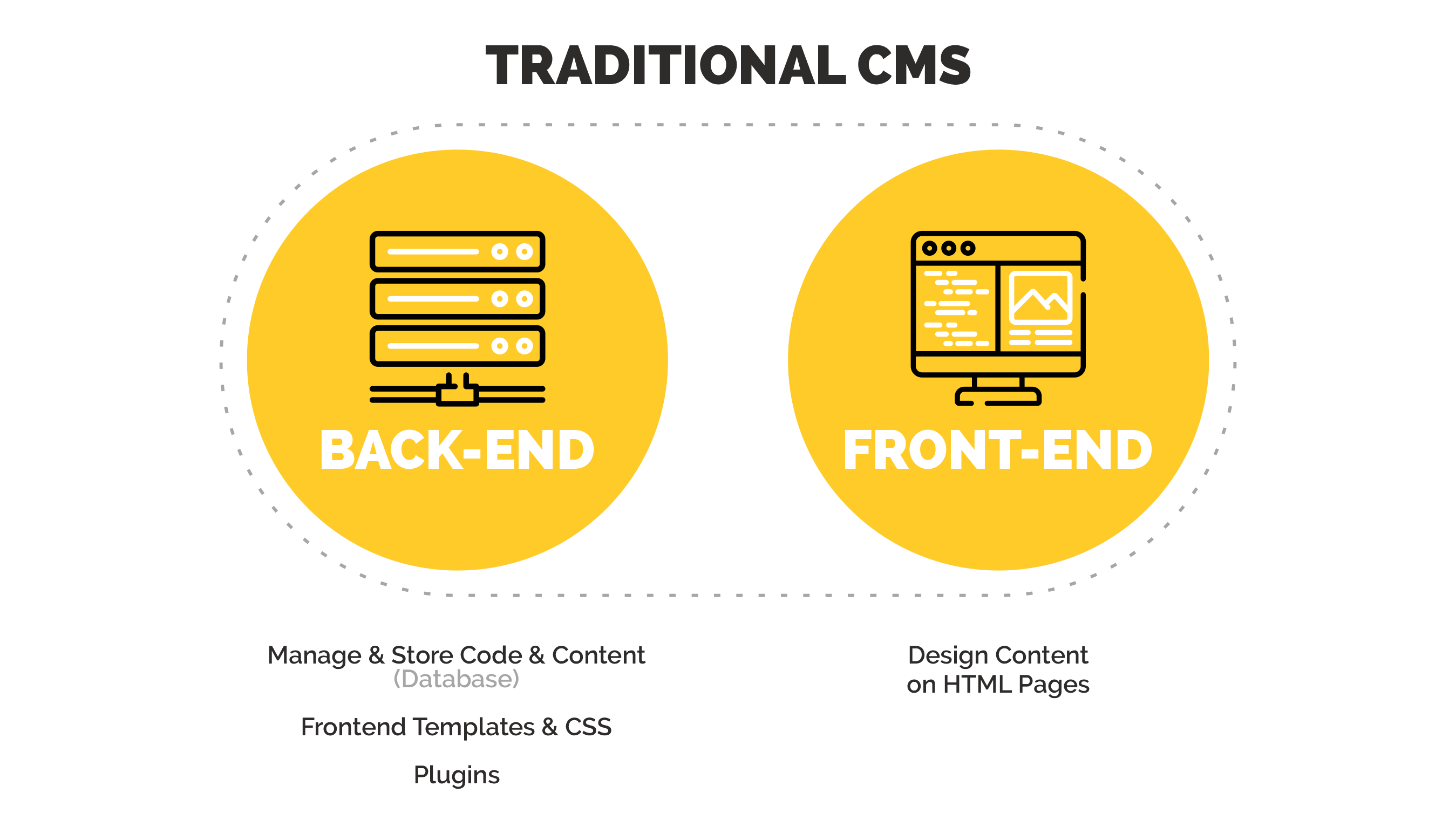
Why Headless CMS is More Secure
- Agility follows a modern approach to interoperability with external systems. As a Headless CMS, Agility maintains a distinct separation of content and your code.
- Agility stores and delivers a website's content independently from that website's codebase. A website based on Agility CMS cannot be used as an attack vector.
- Agility CMS utilizes Auth0 for all authentication operations.
- Agility’s infrastructure utilizes Microsoft Azure, bringing in enterprise-grade security benefits.
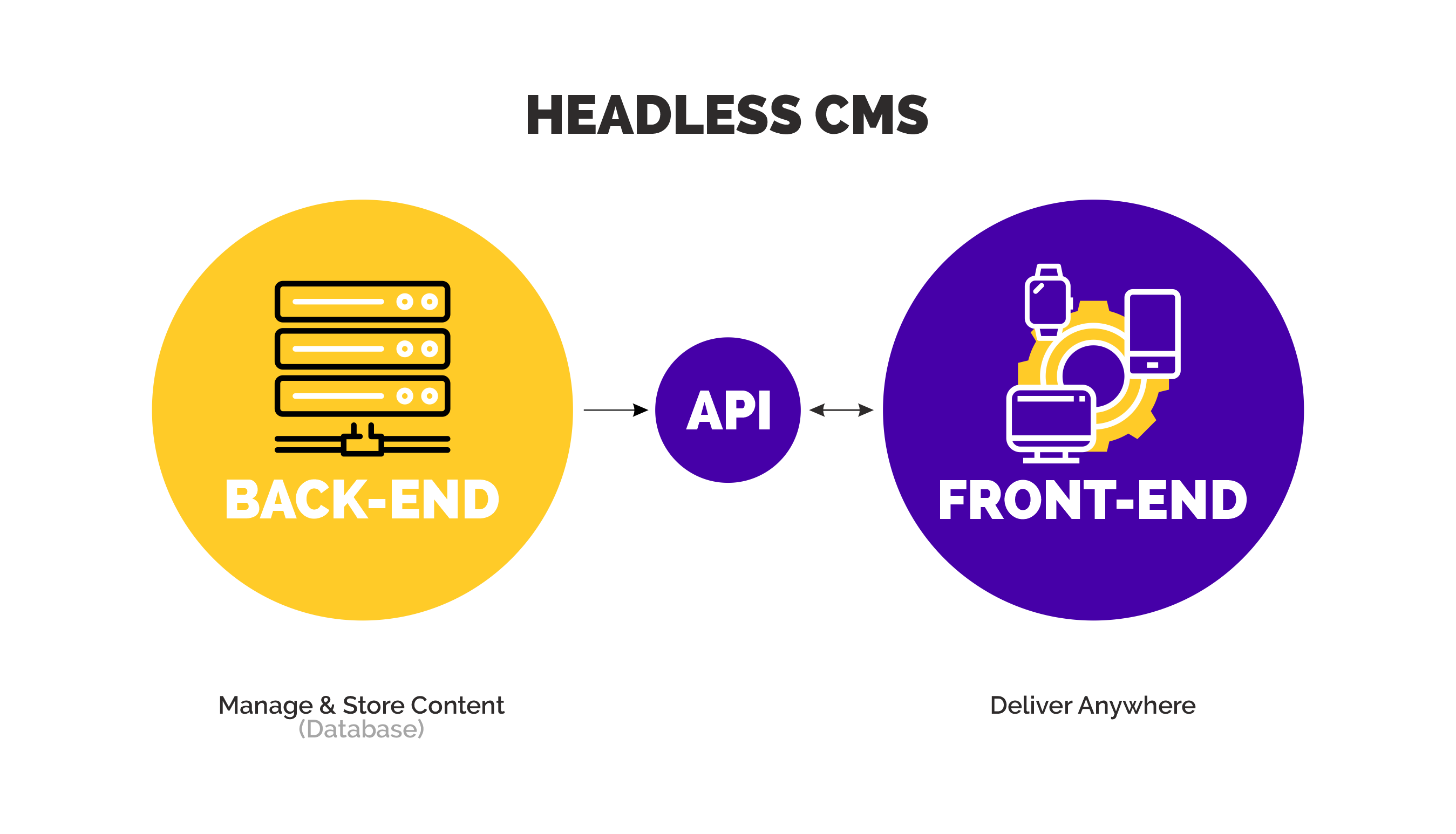
Agility CMS Enterprise Grade Security
Authentication with Auth0
Agility CMS utilizes Auth0 for all authentication operations. Auth0 provides the highest level of security for all login operations, including Multi-Factor Authentication, Enterprise Single Sign-On, and Social Logins.
While more organizations are moving towards remote work, managing authorization has become one of the top requirements for SaaS platforms.
Agility CMS uses Auth0 as our authentication provider. Depending on how your organization works, you can easily match up your security requirements with our platform.
Enterprise SSO is the most secure authentication because your organization controls it. Your employees won't have to remember another username and password, and you won't have to worry about security with an external platform.
This saves time and reduces stress for your employees. It is also much more secure, as any rules you've set up as part of your security and compliance posture will automatically be enforced when you use SSO with Agility.
Your users will authenticate with your organization's gateway, and then Agility will communicate securely with your systems to confirm the user's identity. Many companies refer to enterprise SSO as federated identities or enterprise federation. What this means is that you don't have to worry about duplicated users across all of your systems.
Backed by Microsoft Azure
Agility’s infrastructure utilizes Microsoft Azure, bringing with it enterprise-grade security benefits.
- All data is encrypted in transmission and at rest
- Each customer instance is segregated into its own container, allowing incremental backup, point-in-time restore, and separation from other instances.
- API access keys are customer-maintained, allowing fine-tuned control over where and how your content can be accessed, and for how long.
Azure is an ever-expanding set of cloud computing services to help your organization meet its business challenges. With Azure, your business or organization has the freedom to build, manage, and deploy applications on a massive, global network using your preferred tools and frameworks.
True business transformation requires a stable, secure and flexible IT Infrastructure foundation to build on. True business transformation requires an underlying infrastructure that can complement other modern innovations – Containers, Microservices, DevOps, AI & Machine Learning, Internet of Things (IoT) etc.
Agility can help modernize your infrastructure leveraging Azure, elevating process-centered operations to an agile, customer-focused organization. Our efforts have boosted productivity, improved stakeholder experience, and reduced TCOs for our customers.
Agility is a Microsoft Gold Certified Partner with competencies in Cloud and ISV.
Auto-Scale
The Azure App Service Plans used to host the Agility CMS services are auto-scaling such that they can continue to operate in situations with extreme load or abnormal circumstances.
Encryption and Data storage
Your data is stored in a combination of Azure storage resources, including Azure SQL Databases and Blob Storage. Industry-standard encrypting and hashing is used, with all keys managed using Azure KeyVault.
All data is also stored in an encrypted state (encrypted at rest), as part of the base functionality of Azure Storage and Azure SQL database.
Any data that needs to be secured beyond rest encryption is further encrypted or hashed as necessary using industry-standard methodology. This includes passwords, data connection information, API keys, tokens, etc.
How your data is backed up
Because Agility CMS data is stored in Azure SQL Database, it is automatically backed up and restorable using point-in-time technology to an alternate region. Any data stored in Azure Blob storage is also replicated by the Azure sub-system to a secondary region, in addition to having 3 local copies within the primary data region. Azure is also responsible for encrypting these backups at rest.
Message Encryption
All data that is transmitted between Agility CMS and your services, or 3rd party, is done using TLS 1.2 over HTTPS. Agility CMS uses a combination of Azure CDN and Stackpath CDN for Content Delivery Services of static files and REST API content. These services are protected by TLS 1.2 encryption at all levels. This ensures that no data that is transferred both internally in the Azure system, and externally to the CDN nodes, or to your servers and clients, can be intercepted or altered by a 3rd party.
Penetration tests
While we operate our own penetration testing, performed by 3rd parties, we also provide our enterprise customers, including leading ecommerce, government, and banking institutions, the opportunity to collaborate with us on custom PEN testing to satisfy any extraordinary requirements.
Getting access to backend data
Access to backend data outside of the normal application flow is extremely limited. Only Agility product and support engineers with training and security clearance are granted this permission. These identities are protected by Azure Active Directory using multi-factor authentication.
If you require access to your backend data or have questions about your data, our support staff are happy to answer any question or to escalate any concerns to our engineers.
Ongoing security assessments
Agility utilizes Azure Security Center on an ongoing basis to assess ongoing shifts and improvements in our possible security posture. This allows our engineers and support staff to actively update our systems to comply with deeper levels of security based on new threats and attack methodology.
Audits and monitoring
All access and activity, including any changes to configuration, within our Azure systems is audited and monitored for a history trail. Any code changes are performed via Azure DevOps using Slot based deployment.
PCI Compliance
Agility's Content Manager and Ecommerce component is declared to be PCI Compliant. We do not store or process card or payment credential information. We utilize tokenization and provider-specific vaults to validate, process, and capture transactions.
Security incident reporting
No matter the systems or procedures that are in place, a security incident is still possible. If such an event does occur, Agility is ready to manage this using a pre-defined process. We will notify and affected parties and work closely with them to both mitigate the risk immediately and resolve the problem moving forward.
